- Joined
- Nov 29, 2006
- Messages
- 2,482
My mate recently sent me a message whereas he said that the conflicker worm/virus is going to be released on the April Fool's Day possibly to damage millions of people. Since it was mentioned that it is the 1st of April, my first impression if it is that it is a joke but while the intuition of me not being active on my computer that day is increasing. The message below is what my friend sent me, written by the chef of F-secure.
And it was on the CNN as well, it is everywhere in fact, I just had no idea.
Source: No joke in April Fool's Day computer worm - CNN.com
I don't know what I think, but I will probably have my pc off during that day? What do you say?
my friend said:Computer worm Conficker infects nearly 20 million Microsoft server systems running everything from Windows 2000 to Windows Vista and Windows Server 2008. French air force, Royal Navy warships and submarines, Sheffield Hospital network, UK Ministry of Defence, German Bundeswehr and Norwegian Police all affected. Microsoft has allocated $500,000 to identify its creator. The worm is set to activate on April 1st, 2009, with unknown consequences. Mikko Hypponen, chief research officer at anti-virus firm F-Secure says the true scope of the virus is not known, but in the past 24 hours his company monitored Conficker signals from two million Internet protocol addresses.
And it was on the CNN as well, it is everywhere in fact, I just had no idea.
Source: No joke in April Fool's Day computer worm - CNN.com
CNN said:No joke in April Fool's Day computer worm
* Story Highlights
* The Conficker C computer worm is expected to activate on April Fool's Day
* The worm lets a master computer take over infected zombie PCs
* It's unclear what the program's author plans to do with all the power
* A group called the Conficker Cabal is trying to hunt down solutions
* Next Article in Technology »
By John D. Sutter
CNN
(CNN) -- A computer-science detective story is playing out on the Internet as security experts try to hunt down a worm called Conficker C and prevent it from damaging millions of computers on April Fool's Day.
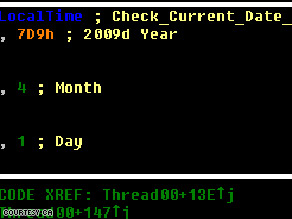
This piece of computer code tells the worm to activate on April 1, 2009, researchers at CA found.
The anti-worm researchers have banded together in a group they call the Conficker Cabal. Members are searching for the malicious software program's author and for ways to do damage control if he or she can't be stopped.
They're motivated in part by a $250,000 bounty from Microsoft and also by what seems to be a sort of Dick Tracy ethic.
"We love catching bad guys," said Alvin Estevez, CEO of Enigma Software Group, which is one of many companies trying to crack Conficker. "We're like former hackers who like to catch other hackers. To us, we get almost a feather in our cap to be able to knock out that worm. We slap each other five when we're killing those infections."
The malicious program already is thought to have infected between 5 million and 10 million computers.
Those infections haven't spawned many symptoms, but on April 1 a master computer is scheduled to gain control of these zombie machines, said Don DeBolt, director of threat research for CA, a New York-based IT and software company.
What happens on April Fool's Day is anyone's guess.
The program could delete all of the files on a person's computer, use zombie PCs -- those controlled by a master -- to overwhelm and shut down Web sites or monitor a person's keyboard strokes to collect private information like passwords or bank account information, experts said.
More likely, though, said DeBolt, the virus may try to get computer users to buy fake software or spend money on other phony products.
Experts said computer hackers largely have moved away from showboating and causing random trouble. They now usually try to make money off their viral programs.
DeBolt said Conficker C imbeds itself deep in the computer where it is difficult to track. The program, for instance, stops Windows from conducting automatic updates that could prevent the malware from causing damage.
The program's code is also written to evolve over time and its author appears to be making updates to thwart some of the Conficker Cabal's attempts to neuter the worm.
[...] (read from source)
I don't know what I think, but I will probably have my pc off during that day? What do you say?















